Attribute-Checker

The AttributeChecker can be set up on a Service Provider (SP) site in order to present an overview of the attributes not transmitted by the respective IdentityProvider (IdP) during login. This phenomenon usually occurs when the missing attributes are not released by IdP. This can in some cases lead to a neccessity of administrative support. Therefore, the sample template on this page includes a means for contacting the IdP Support of your respective institution.
The following is an example of the user interface:
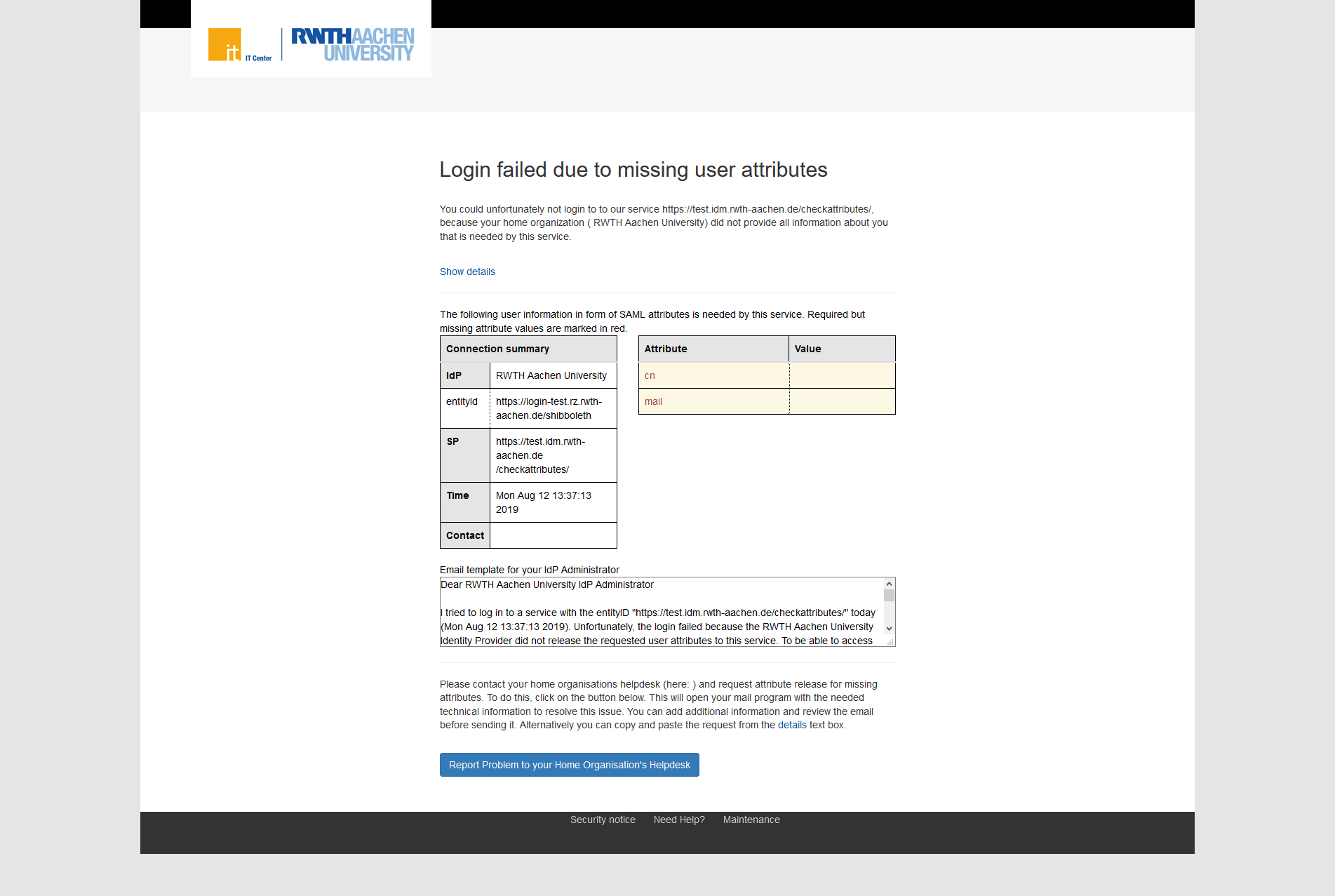
Attribute Checker Handler
The AttributeChecker validates the user session using required attributes.
Login proceeds if the requirements are met, otherwise the page will display an error message.
The attributes are hardcoded and must be defined manually.
Configuration
The AttributChecker can be configured under the points <ApplicationDefaults> and <ApplicationOverride> in shibboleth2.xml.
A session hook has to be added to the file there:
sessionHook="/Shibboleth.sso/AttrChecker".
As well as a metadate attribute-prefix:
metadataAttributePrefix="Meta-"
which is necessary to display the page
Hint: The Template "attrChecker.html" is not generic and has to be altered for each individual SP. Should an SP-installation require more than one SP that checks for attributes, the template will have to be adjusted for each of them individually. |
Configuration Example
Application Defaults
<ApplicationDefaults entityID="https://<HOST>/shibboleth" REMOTE_USER="eppn persistent-id targeted-id" signing="front" encryption="false" sessionHook="/Shibboleth.sso/AttrChecker" metadataAttributePrefix="Meta-" > |
The AttributeChecker -Handler must also be defined in the <Sessions>-element.
The required attributes are defined under the attribute "attributes" (eppn und displayName in this example):
<Sessions ....> <Handler type="AttributeChecker" Location="/AttrChecker" template="attrChecker.html" attributes="eppn displayName" flushSession="true"/> </Sessions> |
To get the metadata for the attrChecker.html-Template, an <AttributeExtractor> must be defined.
<!-- Extracts support information for IdP from its metadata. --> <AttributeExtractor type="Metadata" errorURL="errorURL" DisplayName="displayName" InformationURL="informationURL" PrivacyStatementURL="privacyStatementURL" OrganizationURL="organizationURL"> <ContactPerson id="Support-Contact" contactType="support" formatter="$EmailAddress" /> <Logo id="Small-Logo" height="16" width="16" formatter="$_string"/> </AttributeExtractor> |
Application Override
<ApplicationOverride id="checkattributes" entityID="https://<HOST>/checkattributes/shibboleth" sessionHook="/checkattributes/Shibboleth.sso/AttrChecker" metadataAttributePrefix="Meta-"> |
The AttributeChecker -Handler must also be defined in the <Sessions>-element.
The required attributes are defined under the attribute "attributes" (eppn und displayName in this example):
<Sessions ....> <Handler type="AttributeChecker" Location="/AttrChecker" template="attrChecker.html" attributes="eppn displayName" flushSession="true"/> </Sessions> |
To get the metadata for the attrChecker.html-Template, an <AttributeExtractor> must be defined.
<!-- Extracts support information for IdP from its metadata. --> <AttributeExtractor type="Metadata" errorURL="errorURL" DisplayName="displayName" InformationURL="informationURL" PrivacyStatementURL="privacyStatementURL" OrganizationURL="organizationURL"> <ContactPerson id="Support-Contact" contactType="support" formatter="$EmailAddress" /> <Logo id="Small-Logo" height="16" width="16" formatter="$_string"/> </AttributeExtractor> |
Template Example:
Every attribute that is to be checked must be added manually. The example shows a table with the respective missing attribute.
<!--TableStart--> <tr <shibmlpifnot displayName><shibmlpifnot givenName> class='warning text-danger'</shibmlpifnot></shibmlpifnot>> <td>displayName</td> <td><shibmlp displayName /></td> <td></td> </tr> <tr <shibmlpifnot givenName><shibmlpifnot displayName> class='warning text-danger'</shibmlpifnot></shibmlpifnot>> <td>givenName</td> <td><shibmlp givenName /></td> </tr> <tr <shibmlpifnot sn><shibmlpifnot displayName> class='warning text-danger'</shibmlpifnot></shibmlpifnot>> <td>sn</td> <td><shibmlp sn /></td> </tr> <tr <shibmlpifnot mail> class='warning text-danger'</shibmlpifnot>> <td>mail</td> <td><shibmlp mail /></td> </tr> <tr <shibmlpifnot eppn> class='warning text-danger'</shibmlpifnot>> <td>eduPersonPrincipalName</td> <td><shibmlp eppn /></td> </tr> <tr> <td>eduPersonTargetedID</td> <td><shibmlp persistent-id /></td> </tr> <tr> <td>eduPersonScopedAffiliation (optional)</td> <td><shibmlp affiliation /></td> </tr> <!--TableEnd--> |
The text to the IdP must also be individually changed:
The attributes that were not released to the service are: * <shibmlpifnot cn>cn</shibmlpifnot> * <shibmlpifnot mail>mail</shibmlpifnot> |
The names of attributes follow the conventions used in attribute-map.xml.

