Login via the Terminal
The most common and straightforward way to log into the HPC Cluster is by using a terminal emulator, given that most programs operate on the command-line.
Connections are secured using the Secure Shell (SSH) protocol. Depending on your operating system, various clients are available. This tutorial primarily covers OpenSSH and PuTTY, but the instructions are generally applicable to other clients such as MobaXTerm.
The HPC Cluster features multiple login-nodes to ensure redundancy and balance load. If you encounter a busy login node, consider connecting to an alternate node.
Prerequisites:
- Access must be through the RWTH network or a network of its partners.
- Registration for the HPC service is required.
- Configuration of a second factor authentication (2FA) in the RegApp is necessary.
Table of Contents
Linux, Windows, and MacOS come with OpenSSH clients that you can use to connect to the cluster. For this, start your terminal application. On Windows the Microsoft Terminal and on MacOS iTerm2 are popular choices.
Afterwards, use the following command to connect to one of the login nodes, e.g., login23-1:
ssh <user-id>@login23-1.hpc.itc.rwth-aachen.de
Replace <user-id> with your RWTH username (e.g. ab123456). After entering the command, you will be prompted to input your HPC password followed by your 2FA code.
PuTTY is a widely used, free, and open-source terminal emulator and SSH client for Windows. To connect to the HPC Cluster using PuTTY:
- Download and install PuTTY.
- Open PuTTY and in the "Hostname" field, enter the address of one of the HPC login-nodes
(e.g.login23-1.hpc.itc.rwth-aachen.de) - Click "Open" to initiate the connection.
- When prompted, enter your RWTH username followed by your HPC password and your 2FA code to authenticate.

Managing multiple entries of passwords and 2FA codes throughout the day can be cumbersome. Using SSH key pairs simplifies this process by requiring fewer authentications. After storing your public key in the RegApp, you'll need to enter your HPC password only once every ten hours.
However, if you have (and indeed you should have) passphrase-protected your private SSH key during key generation, this passphrase is then needed for every connection. SSH agents alleviate this need by securely storing your private SSH key.
Note: If you use an ssh config file, do not set "PreferredAuthentications publickey" for the CLAIX nodes. This will otherwise prevent the password request and thus the login.
OpenSSH Agents
On Linux and MacOS: You can use the following commands to start the OpenSSH agent and add your private key:
eval `ssh-agent`ssh-add <private_key>
Replace <private_key> with the actual path to your private SSH key. Usually it is stored at ~/.ssh/
On Windows: follow the official documentation.
Putty Pageant
For those using PuTTY, Pageant acts as an SSH agent:
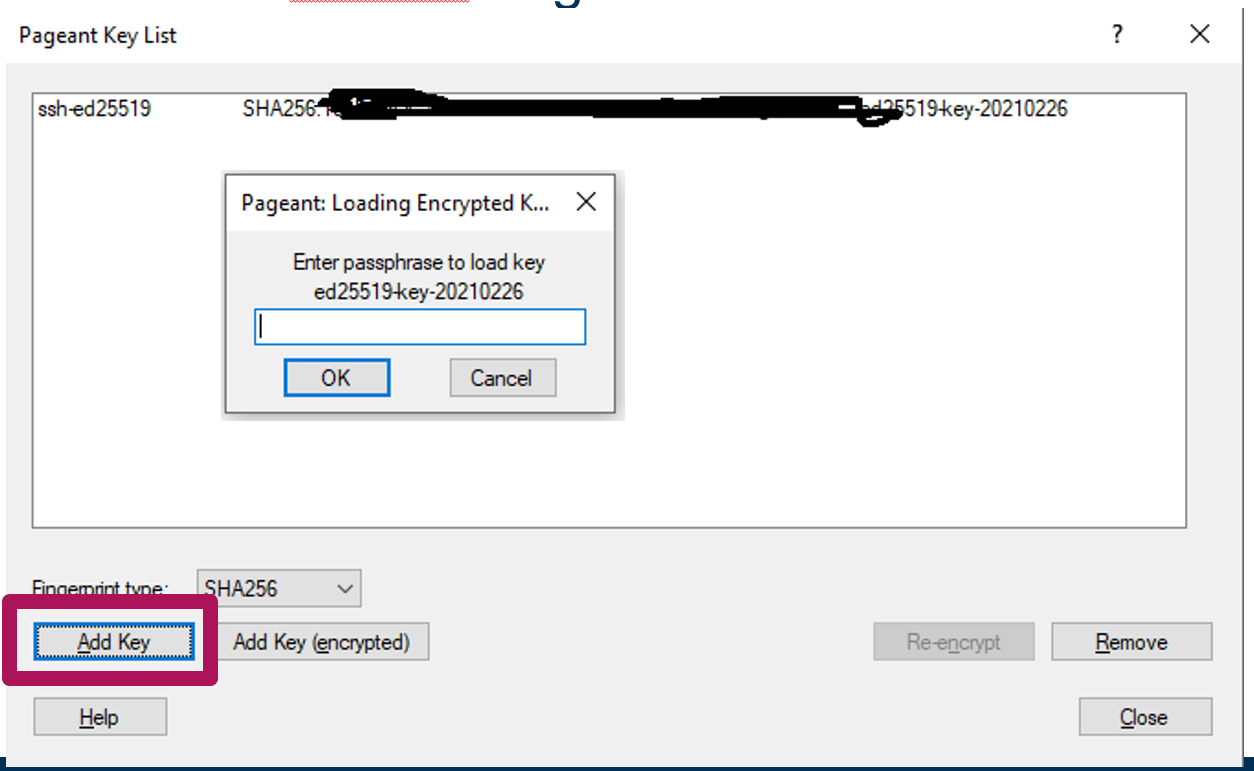
- Open Pageant and click "Add Key".
- Select your Putty-Private-Key (.ppk file) and enter the passphrase you set for the key.
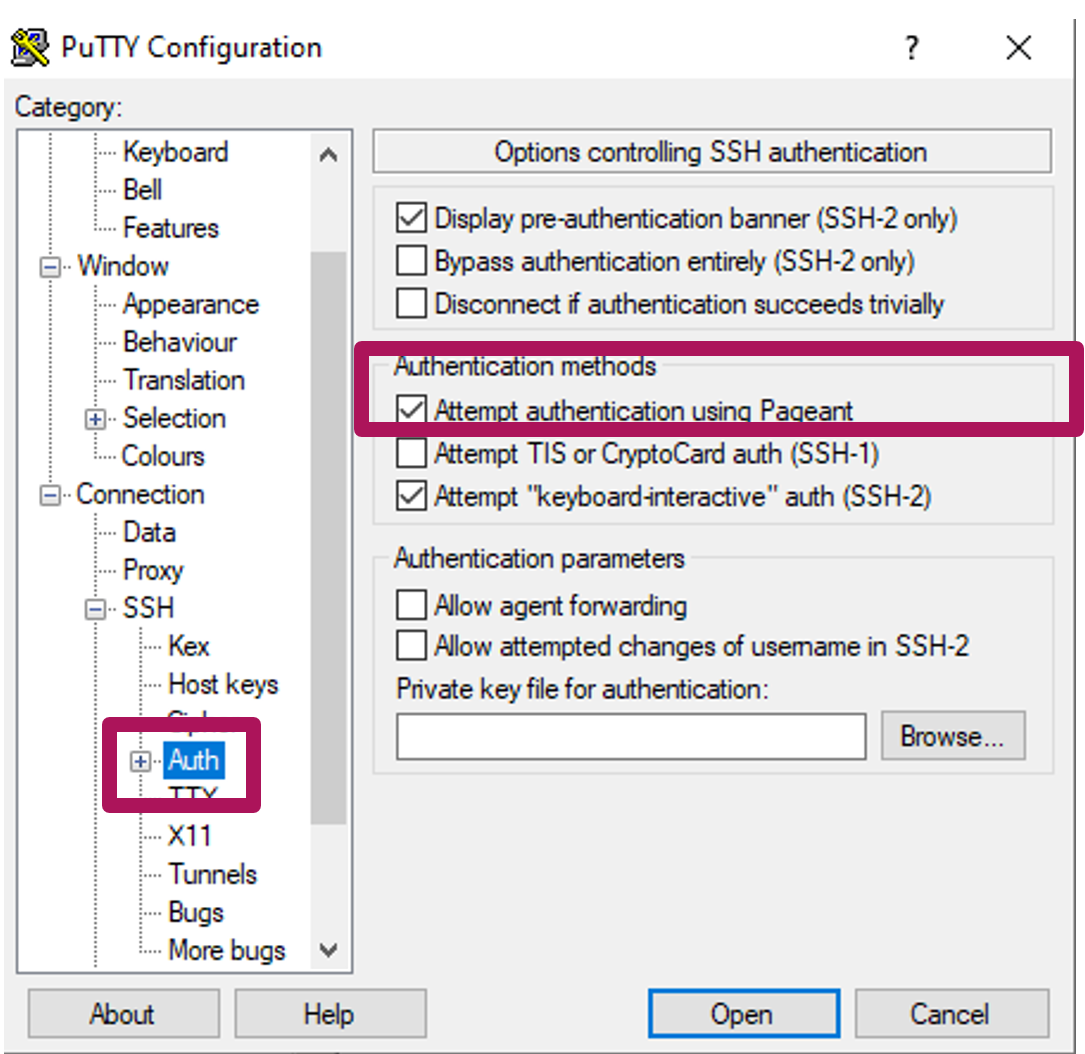
- In PuTTY, navigate to Connections → SSH → Auth and enable "Attempt authentication using Pageant".
- If you are using MobaXTerm, please refrain from using remote-monitoring. This option leads to frequent I/O-Operations which throttles the file servers.

