Hardware Token for RWTH Single Sign-On (WebAuthn/FIDO2)

The hardware token for RWTH Single Sign-On (WebAuthn/FIDO2) is used with a physical (hardware) security key by default. Information on these security keys can be found here.
To set up this token, both part of the setup in the token manager and verification outside the token manager must be carried out.
- Requirements for the use of the hardware token
- Configuration in the Tokenmanager
- Verification outside the Token Manager
Alternatively, you can also use Apple or Android end devices (e.g. smartphones) with touch or face ID for this token instead of a security key. Please check first whether your device supports these functions.
1. Requirements for the use of the hardware token
- You have a hardware security key (hardware token).
- Compatible with both token types “Hardware token for VPN and RWTH Single Sign-On (HOTP)” and “Hardware token for RWTH Single Sign-On (WebAuthn/FIDO2)” are e.g. YubiKeys, Nitrokeys (Pro 2 and 3) and selected Feitian Keys.
- To set up this token, the security key must at least support the WebAuthn/FIDO2 protocol.
2. Configuration in the Tokenmanager
Video tutorial on token setup for the RWTH Single Sign-On.
Step 1
Insert your security key into the USB slot of your PC.
Step 2
Go to the Token Manager.
If you have already set up one or more tokens, you will be asked to enter a one-time security code.
Please select the token you wish to use from the drop-down menu, enter the one-time security code from the token.

Step 3
Now click Next.
Step 4
Click on the blue Create button at the bottom left of the Token Manager.

Step 5
Choose Hardware Token for RWTH Single Sign-On (WebAuthn/FIDO2).

Step 6
Click on Next.
Step 7
Enter a unique description for the security key (e.g. My hardware key).
This helps you to differentiate between tokens, especially if you have created several tokens.

Step 8
Click on Create.
Step 9
Start the verification prozess for the hardware token in the credential manager or browser by clicking on Register.
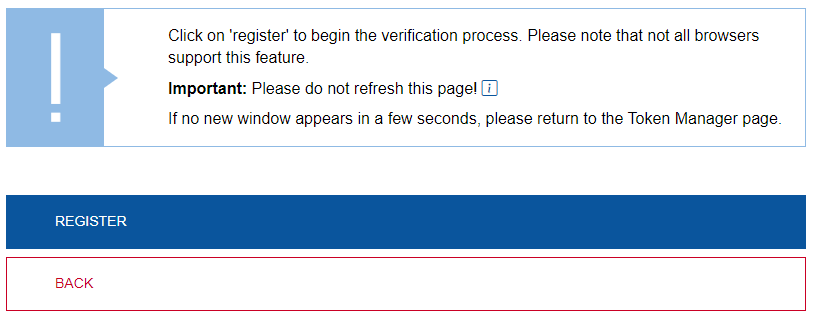
3. Verification outside the Token Manager
By clicking on Register, you leave the Token Manager and must now confirm the token.
You can either carry out the verification with a Credential Manager or do this in the browser on your end device. How you proceed is up to you, but may vary depending on the end device.
The following instructions provide examples of verification:
Verification using Windows credential manager
Step 1
To set up your hardware token, please follow the on-screen instructions.
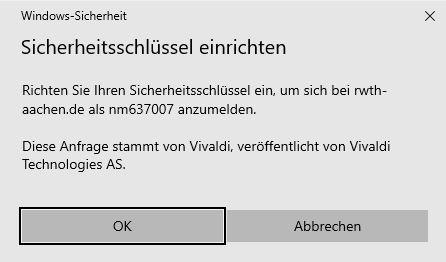
Step 2
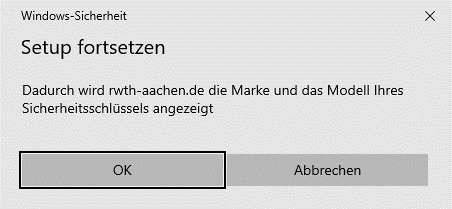
If the data is correct, confirm with OK.
Step 3
Whether a PIN is required depends on whether and how the hardware key was previously set up.
If you are prompted to enter your PIN, enter the secure PIN you chose previously.
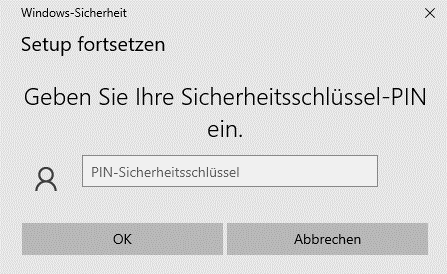
Step 4
If the data is correct, confirm with OK.
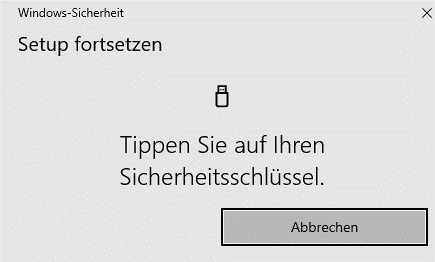
Step 5
Then follow the instructions on the screen and tap the security key with your hand.
On the Yubikey, tap the circular golden recess with the Y on it.
If your operating system does not have its own credential manager, such as that of Windows, the tokens are set up by your web browser.
Step 1
Do not anonymize your data in the first step, otherwise the token setup will fail:
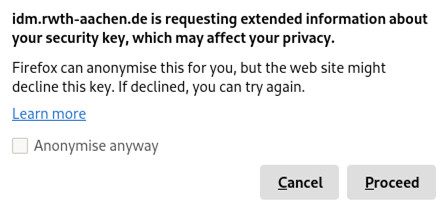
Step 2
Then click on Proceed.
Step 3
The hardware key can now be connected to the system.
Whether a PIN is required depends on whether and how the hardware key was previously set up.
If you are prompted to enter a PIN, enter the secure PIN you have chosen yourself.
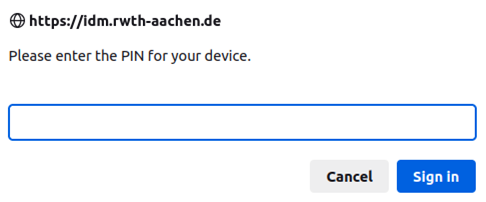
Step 4
Then click on Sign in.
Step 5
Complete the process by tapping the security key.
On the Yubikey, tap the circular golden recess with the Y on it.

Step 1
If there is no key connected to the system yet, you will be asked for the type of device to be used. Please select USB security key:
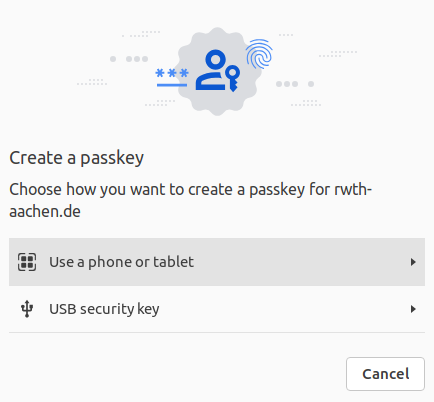
Step 2
Then follow the instructions on your screen.
Configuration with Apple Touch- or Face-ID
By using Apple Touch ID or Face ID as a hardware token for RWTH Single Sign-On, secure login to RWTH services can be enabled without a separate hardware security key.
Please check first whether your device supports these functions.
If you already use the Apple Keychain function, you can integrate Touch ID or Face ID as a hardware token for RWTH Single Sign-On (WebAuthn/FIDO2) as follows:
Step 1
Select an end device on which Touch ID and / or Face ID is already set up or with which this can be done.
Apple smartphones are best suited for this.
Apple computers that have fingerprint scanners (Mac computers with Magic Keyboard, Apple Chip and MacOS Big Sur 11.4 or newer) can also be used for Touch ID.
Step 2
If this has not yet been done, the Touch ID or Face ID function must be activated in the system settings.
For MacOS devices:
- Select the Apple menu (apple icon) > System Preferences > Touch ID & Password
For iOS devices:
- For Touch ID:
- Select Settings (gear icon) > Touch ID & Code > Configure Touch ID
- For Face ID:
- Select Settings (gear icon) > Face ID & Code > Configure Face ID
Step 3
Follow the respective instructions on the screen of your end device. The required biometric data (fingerprints or facial images) must be added.
Step 4
Once this is complete, call up the Token Manager on the respective end device and follow the steps under Configuration in the Tokenmanager.
As soon as you have started the registration, continue with the next step here.
Step 5
After you have clicked on Registration, a new window will open where you can Select a device for your passkey.
Select Apple Keychain here, or if this is not possible, select This device.

Step 6
Follow the instructions displayed on the screen.
It may be necessary to place your finger on the Touch ID sensor or face the camera.
After confirmation, the overview in the token manager is displayed again and the token is now set up.
The next time you log in to an RWTH service, you must select the Hardware token for RWTH Single Sign-On (WebAuthn/FIDO2) option.
Authentication is then carried out using the previously set up fingerprint or facial image.
Configuration with Android Touch- or Face-ID
By using the Android Touch-ID or Face-ID as a hardware token for the RWTH Single Sign-On, a secure login to RWTH services can be enabled without a separate hardware security key.
Please check first whether your device supports these functions.
You can integrate Touch ID or Face ID as a hardware token for RWTH Single Sign-On (WebAuthn/FIDO2) as follows:
Step 1
Select an end device on which Touch ID and / or Face ID is already set up or with which this can be done.
Step 2
If this has not yet been done, the Touch ID or Face ID function must be activated in the system settings.
Select Settings (gear icon) > Security and privacy > and then select Biometric data under the Additional security settings tab.
- For Touch ID, select Fingerprints
- For Face ID, select Face recognition
Step 3
Follow the instructions on the screen of your device. The required biometric data (fingerprints or facial images) must be added.
Step 4
Once this is complete, call up the Token Manager on the respective end device and follow the steps under Configuration in the Tokenmanager.
As soon as you have started the registration, continue with the next step here.
Step 5
After you have clicked on Registration, a new window will open where you can Select a device for your passkey.
Select This device here.

Step 6
Follow the instructions displayed on the screen.
It may be necessary to place your finger on the Touch ID sensor or face the camera.
After confirmation, the overview in the token manager is displayed again and the token is now set up.
The next time you log in to an RWTH service, you must select the Hardware token for RWTH Single Sign-On (WebAuthn/FIDO2) option.
Authentication is then carried out using the previously set up fingerprint or facial image.
In case of further problems please contact the IT-ServiceDesk.

