Activating an Administration Account

This guide describes how to complete and activate your administrator account with Cisco after it has been created in the Cisco Secure Endpoint Console.
The following steps are necessary for this:
1. Activate the account
Step 1
After your account has been created in the Cisco Secure Endpoint Console, you will receive an invitation e-mail to the e-mail address specified in the creation process (sender: no-reply@amp.cisco.com, subject: Welcome to Cisco Secure Endpoint).
In the e-mail, click on the link under Step 1 Create a Security Cloud Sign On account here.

Step 2
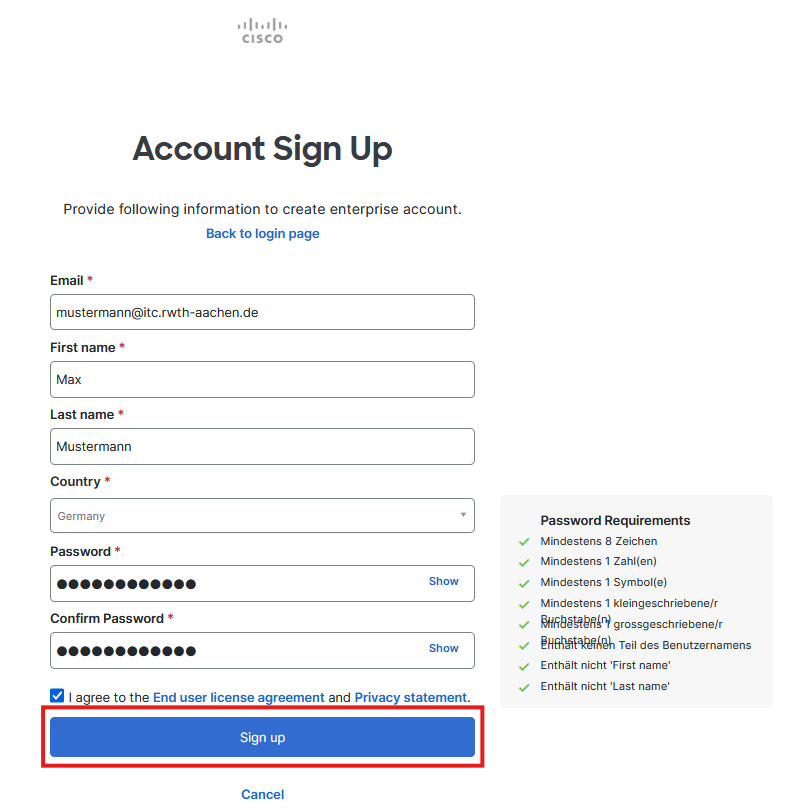
You will be redirected to the website with a registration form. Complete the form and then click on Sign Up.
- Hint: Some special characters ((e.g. +=-() ) are prohibited in the password. If you use these characters, you will receive a message that the guidelines are not met.
Step 3
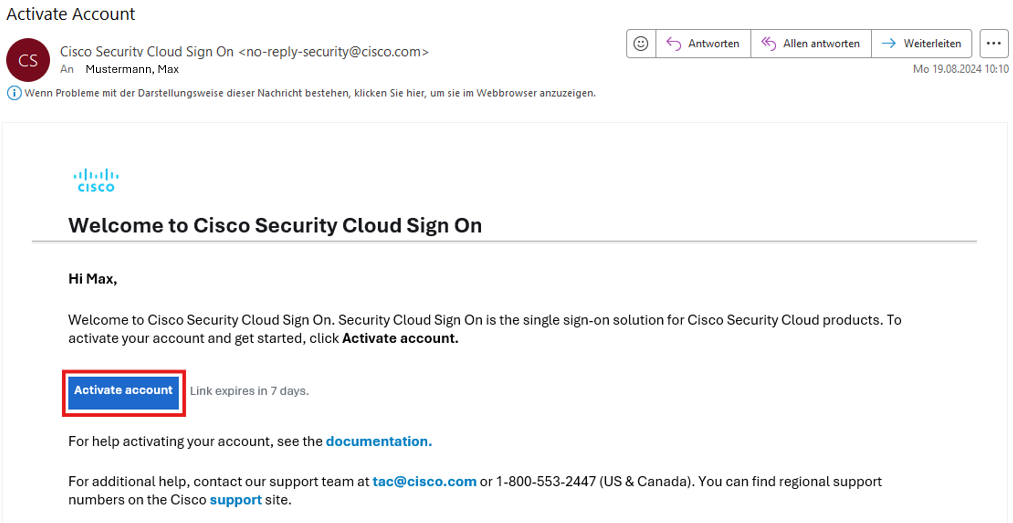
You will then receive another e-mail (sender: Cisco Security Cloud Sign On <no-reply-security@cisco.com>”, subject: Activate Account).
Click on the Activate Account link in the e-mail.
Step 4
You will be redirected to a website. Click here on Activate Account.

Step 5
Your account will be activated. In the meantime, several redirects can be observed in the address bar of the browser. This is not an error! Wait until the page is fully loaded and the message Welcome to Duo Security appears.
Click on Erste Schritte (Get started) on the page.

2. Set up multicaktor authentication
You have three options for multi-factor authentication:
- Phone number: With this option, you can use a telephone number as a second factor. This can either be a cell phone number or your work phone number.
- Security key: Here you can use a USB key that supports WebAuth as a second factor, e.g. a YubiKey
- Google Authenticator: This option is only offered after you have implemented one of the two options mentioned above. The method will then replace the security key or the telephone number when logging in! Even if the method is called Google Authenticator, the TOTP method is always supported, i.e. you can also use another authenticator app or a password manager with a corresponding TOTP plugin.
Phone number option (using a work phone number as an example)
Step 1
Select the Phone number option.

Step 2
Enter your work phone number (including area code, but without the leading 0), check the This is a landline phone box and click Continue.

Step 3
Skip the window for entering an optional extension number by clicking Skip this step.

Step 4
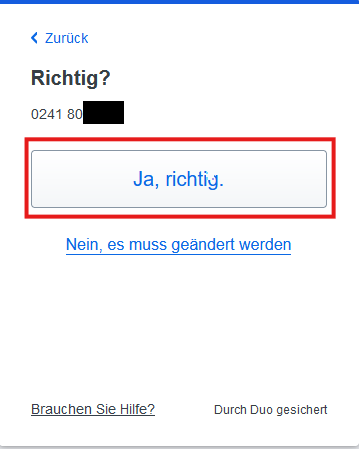
Check the phone number carefully. If the number is correct, click Yes, correct and in the next window click Call me.

Step 5
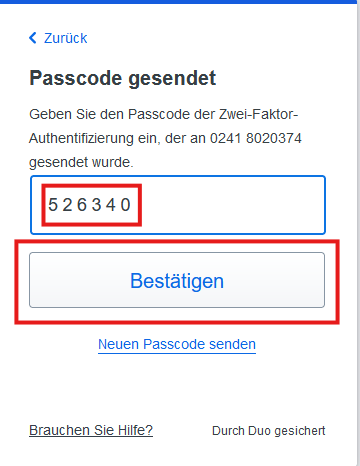
You will receive a call in which you will be given a passcode. Enter the passcode in the corresponding field and click Confirm.
Step 6
Finish setting up the second factor by clicking I don't want to add any more devices.


Step 7
Now that the initial second factor has been set up, you need to log in with your account. To do this, click on Log in now with Duo.

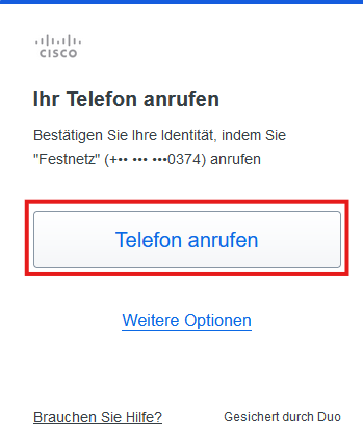
Step 8
You will now be prompted to start a phone call to check the second factor. Confirm this with Call telephone.
Step 9
You will now receive another call from Cisco asking you to press any key on your phone to confirm, for example 1. After you have pressed the key, the verification is successful and your browser will redirect you to the next page.
You now also have the option of setting up a second factor using TOTP (Time-based one-time password), which you can manage with an authenticator app such as Google Authenticator or a password manager such as Keepass.
If you would like to use the TOTP method in the place of the method you have just set up, click on set up Google Authenticator and follow these instructions below Option Google Authenticator.
If you do not want to set up an additional TOTP procedure, click Finish.

Please note: After successful activation, the Cisco Application Portal website opens. Here you will see the message “You're not assigned to any Enterprise”. This message is normal in our deployment and can be ignored! |
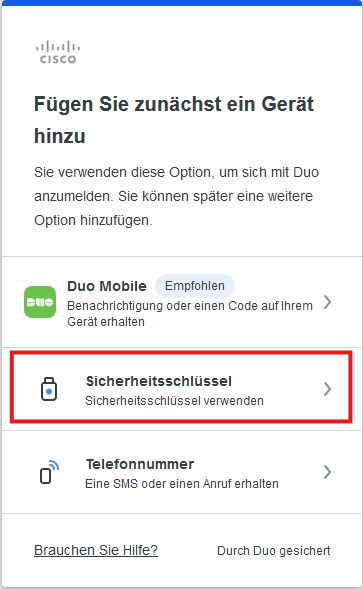
Security key option (Using a USB key as an example)
Step 1
Select Security key , make sure your USB key is inserted and click Continue.
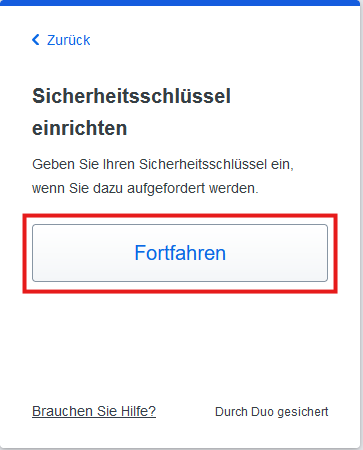
Step 2
A Windows pop-up appears in which you can select the device on which the key is to be saved. Select the Security key option here.
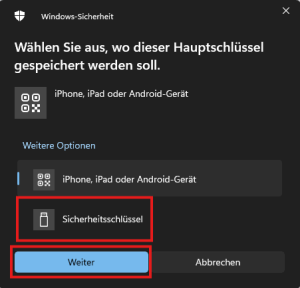
You will then be prompted to tap on your USB key.
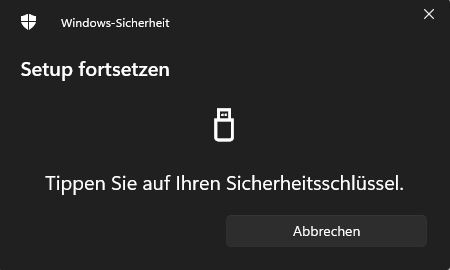

Step 3
After the master key has been saved, a corresponding success message appears in the browser. Click on Continue.
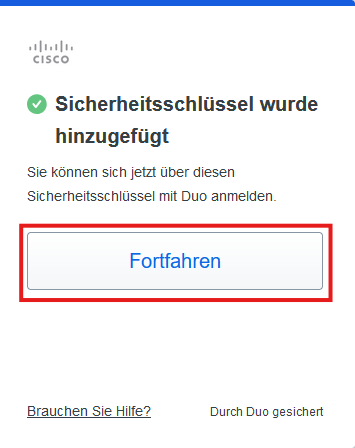
Step 4
Finish setting up the second factor by clicking on I don't want to add any more devices and in the next window click on Log in with Duo.
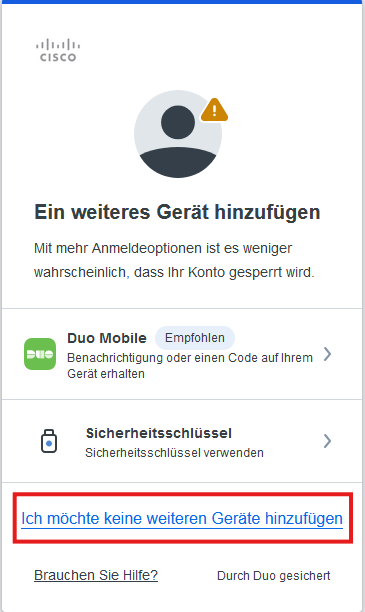
You now also have the option of setting up a second factor using TOTP (Time-based one-time password), which you can manage with an authenticator app such as Google Authenticator or a password manager such as Keepass. This is not mandatory.
If you would like to use the TOTP procedure in place of the procedure you have just set up, click on set up Google Authenticator and follow these instructions below Option Google Authenticator.
If you do not want to set up an additional TOTP procedure, click Finish.

Please note: After successful activation, the Cisco Application Portal website opens. Here you will see the message “You're not assigned to any Enterprise”. This message is normal in our deployment and can be ignored! |
Google Authenticator option (TOTP)
Step 1
To set up TOTP as an additional procedure, select iPhone or Android in the following window and click Continue.

The choice of mobile platform only controls which app store link for the Google Authenticator app is displayed. The subsequently generated code works independently in every TOTP-enabled application, including those already installed.
Step 2
Scan the displayed QR code with an authenticator app on your smartphone.
If you do not have the option to scan, click on Can't scan and you will be shown the security key as a character string, which you can then enter manually in the password manager of your choice.
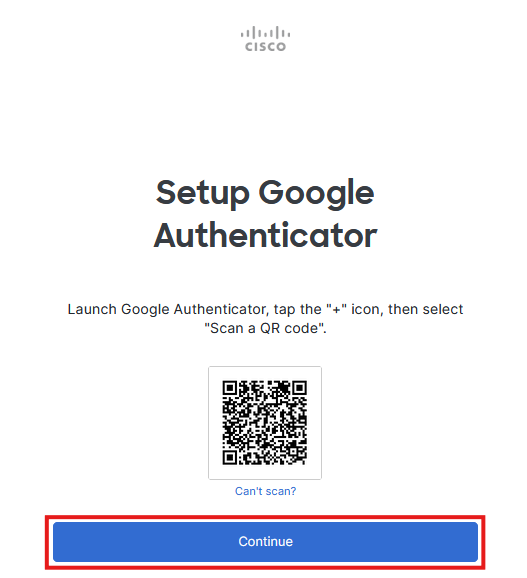
Step 3
Once you have created your TOTP entry, click Continue.

Step 4
You will now be asked once to enter a generated OTP code for confirmation. Enter the code and click on Verify.

Please note: After successful activation, the Cisco Application Portal website opens. Here you will see the message “You're not assigned to any Enterprise”. This message is normal in our deployment and can be ignored! |

