General Operation Information

On this page you will find general information on the operation of Cisco Secure Endpoint:
Guidelines (Policies)
As delivered, the Cisco Secure Endpoint Console includes a set of default use case policies for each supported operating system that you can use:
- Audit: These policies are used for testing. They are configured so that all features are switched on but no changes are made, though detected threats will be displayed in the events.
- Protect: These policies contain default settings that can be used for operation on normal user devices. You may need to make adjustments to the required exceptions here.
- Server: These policies contain default settings that are optimized for the operation of standard server systems. You may need to make adjustments to the required exceptions here.
- Domain Controller: These policies contain default settings that are specially optimized for the operation of Active Directory server systems.
- Triage: These policies contain aggressive settings for the virus scanner. They are intended for systems that are to be scanned particularly thoroughly following a suspected threat.
- Default Network: The policy contains settings for network devices. It can be ignored as network devices are not included in the current implementation. There must, however, be at least one network policy in the tenant.
You should use additional policies if you only want to apply settings for certain systems or applications. They can either be created by duplicating an existing policy and then adapting it, or a new policy can be created. With new Windows policies, the user notification is deactivated by default if a virus is detected. We recommend switching this on by checking the Engine Notifications box in the policy under Advanced Settings → Client User Interface.
Groups
Groups are used to assign policies to devices within them. A policy for each supported operating system always applies to each group. A specific policy can be assigned to a group if no policy is assigned for a specific operating system; in this case either the default policy configured under Administration → Organization Settings or, in the case of nested groups, the corresponding policy of the parent group applies.
As delivered, the Cisco Secure Endpoint Console contains some default groups that can be used for the assignment of systems. The names of the default groups correspond to the names of the default policies described above and the policies are configured accordingly for these groups and are intended for the respective use case.
Product updates
Cisco releases product updates for Cisco Secure Endpoint at irregular intervals, which contain corrections for security vulnerabilities, bugs or new features. These updates are not automatically distributed to the end devices for Windows, Linux and MacOS, but must be actively controlled. You have 2 options for updating these operating systems:
- Control via policy: The policies for the operating systems mentioned contain the item Product Updates, with which the update can be controlled. Here you can select the version to be used on your devices. (The None entry means that no changes are made to the currently installed version) You must also specify a time window in which the client should check for new versions and, if applicable, perform the update. In the Windows policy, you can also select whether and when a required reboot should be carried out automatically. According to Cisco, a reboot should generally no longer be necessary in current product versions, but may occur in exceptional cases.
- Update via installer: An update installation is also possible via the normal installer. To do this, simply download the corresponding installation package as described under Installing Cisco Secure Endpoint and start the installation manually or have it carried out via an existing software distribution.
Operation on Systems without an Internet connection
Cisco Secure Endpoint requires an Internet connection to the Cisco Cloud in order to function correctly. In order to protect servers without a direct internet connection, a proxy server can be configured by policy so that only a dedicated exception for access to TCP port 8080 in the network 134.130.122.216/29 must be made in the outgoing firewall policies of the corresponding network. The following coordinates must be entered in the proxy policy settings in order to use the proxy:
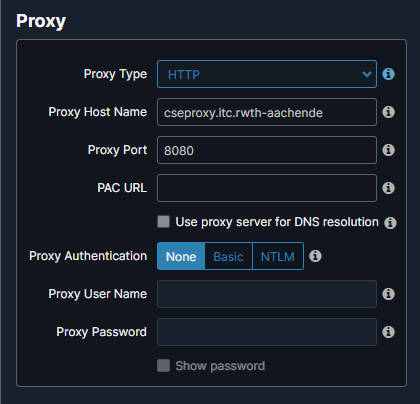
The provided proxy servers are only accessible from clients within the RWTH network and are technically restricted for access to named web addresses of the Cisco Cloud, which are necessary for the operation of Cisco Secure Endpoint. They do not route any other Internet traffic and should only be used for the use case described. In addition, no TLS termination is performed here; all encryption is negotiated and secured directly by the client and the Cisco Cloud endpoint.

